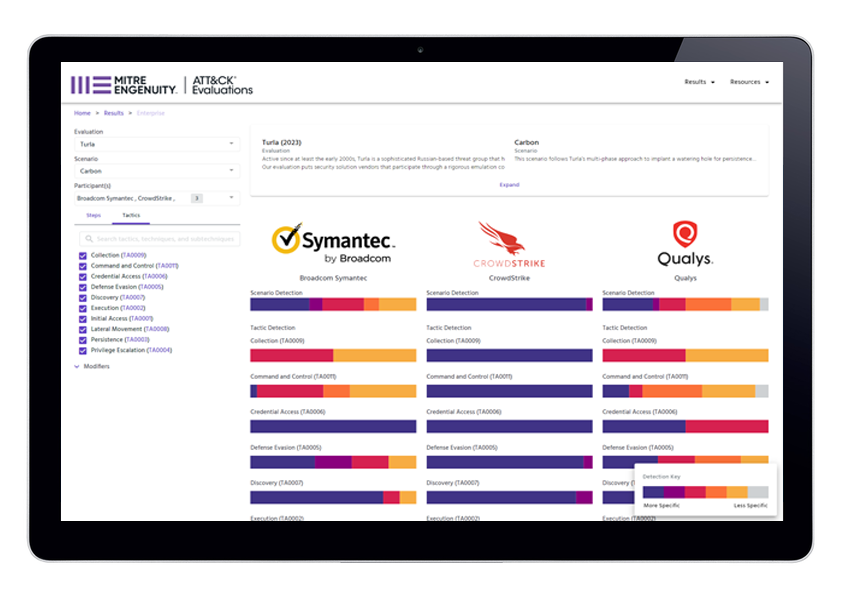
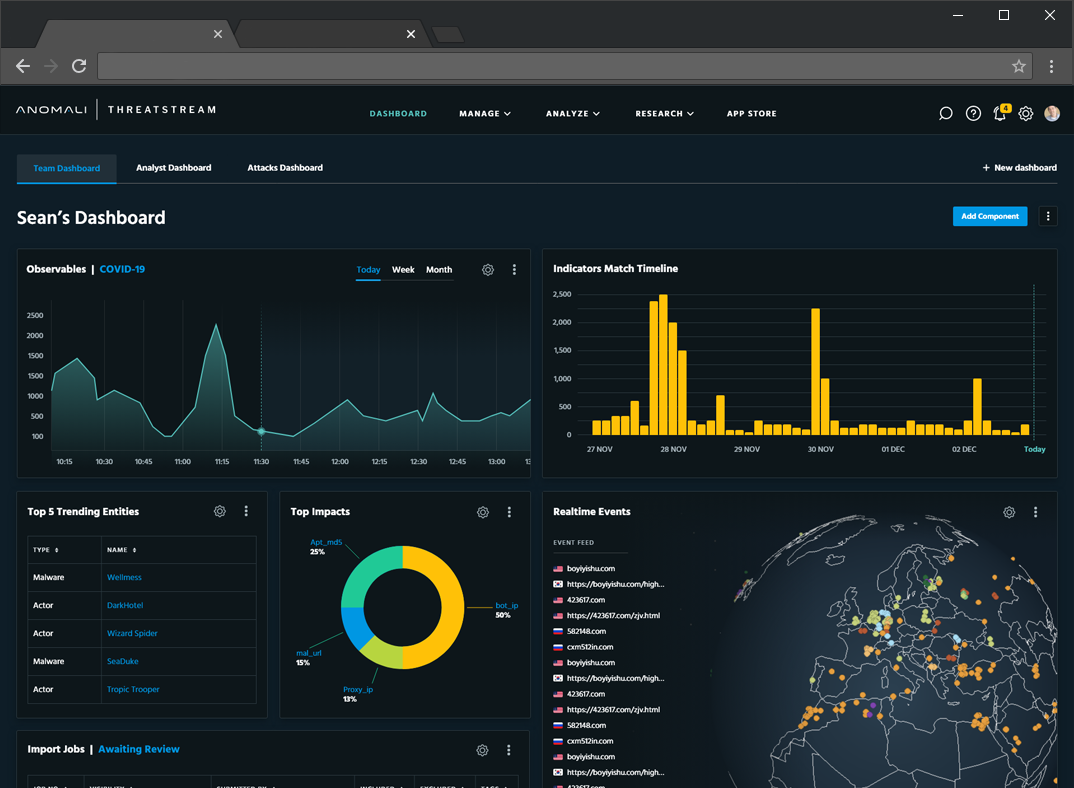
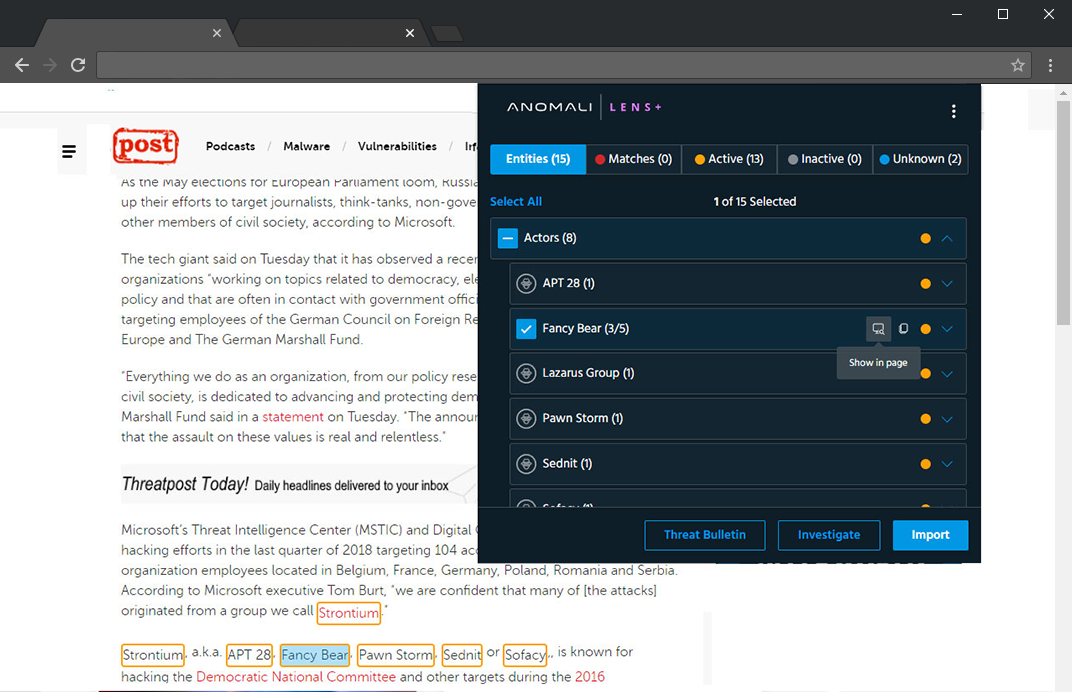
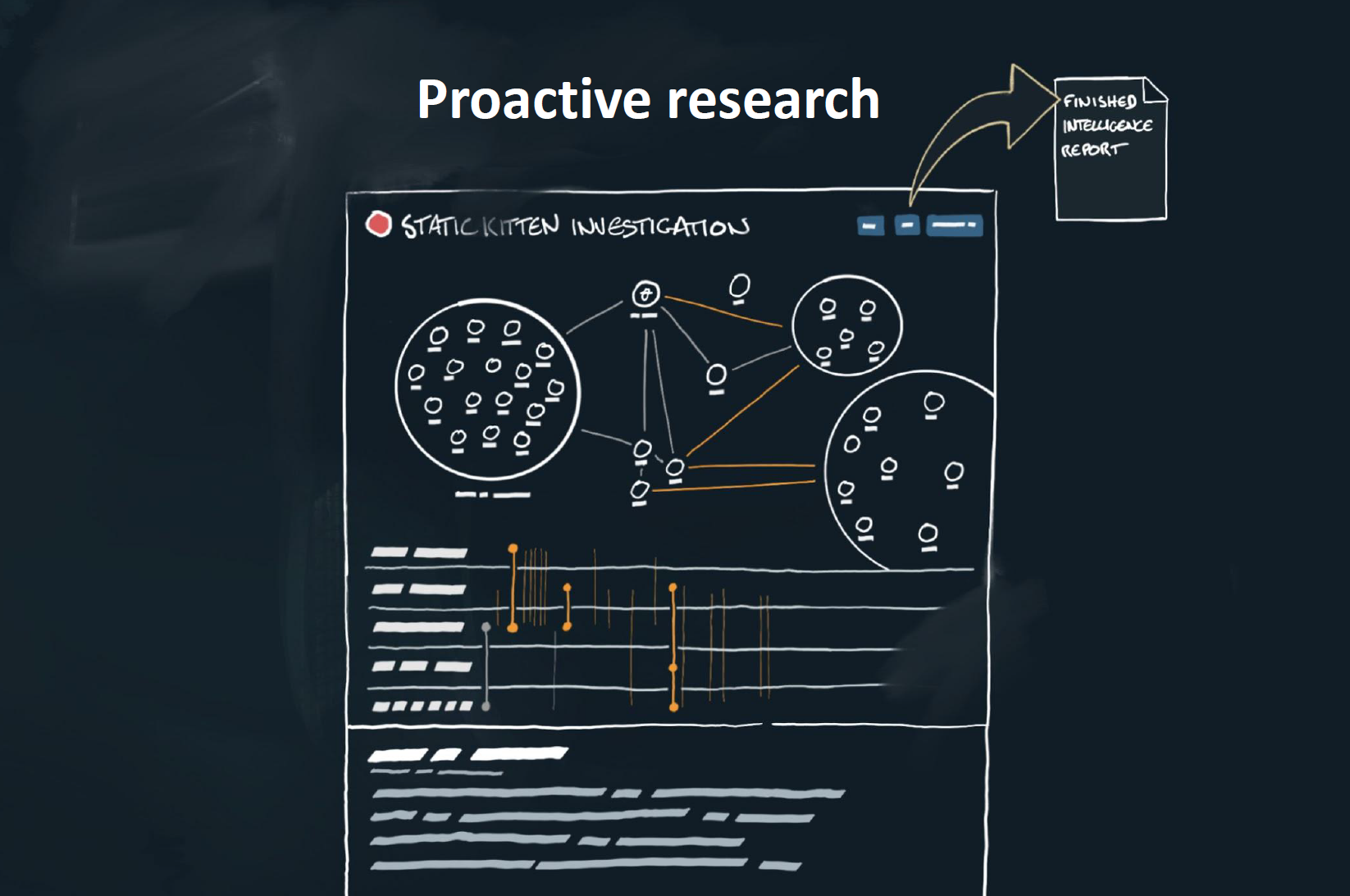
defend against adversary behaviors through a transparent evaluation process
// MITRE ATT&CK Evaluations
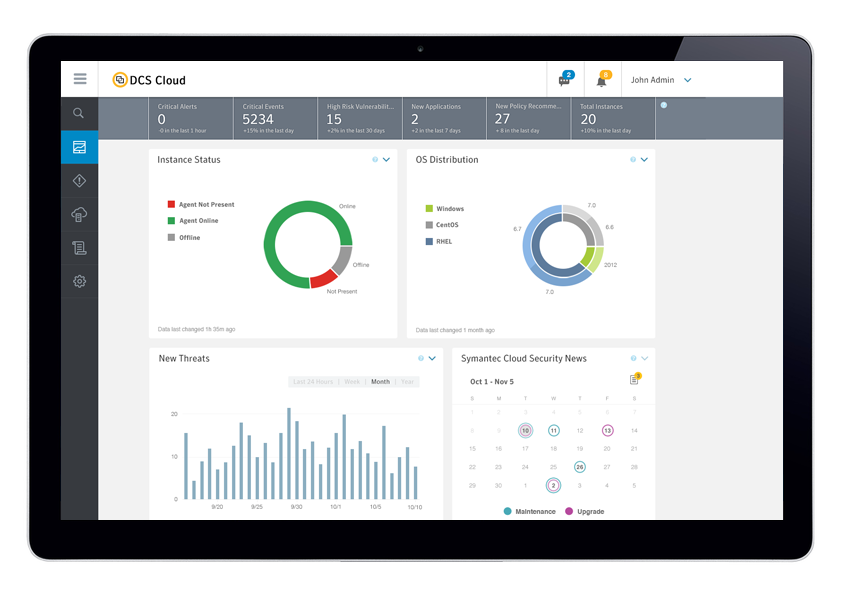
take control of public cloud infrastructure from a single console
// Cloud Workload Protection
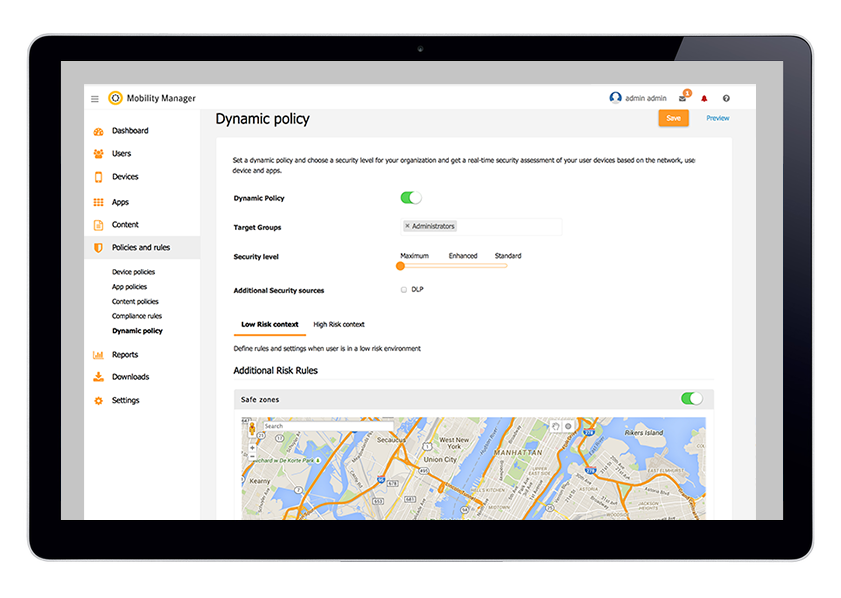
achieving the right balance of security and user
experience
// Contextual Policy
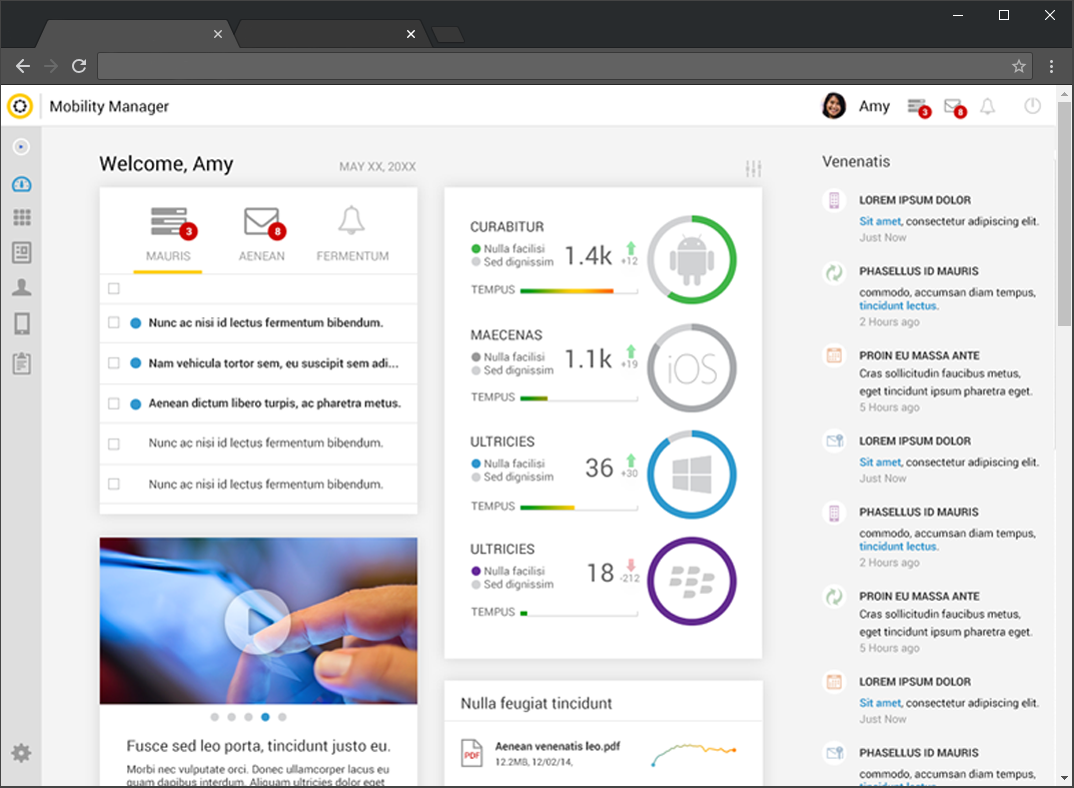
consumer ease of use with enterprise security
// Mobility Manager
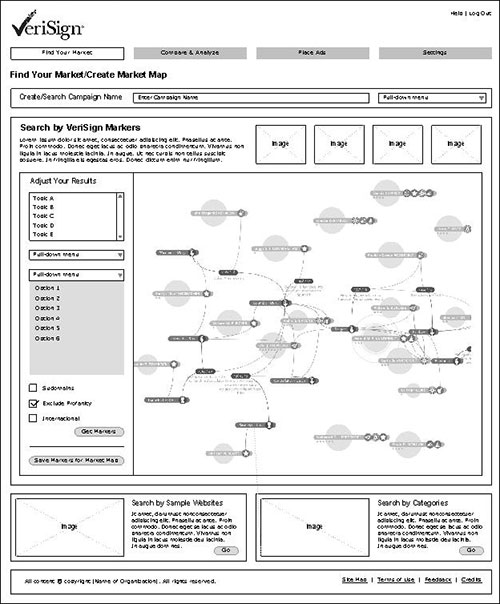
the smart way to create market maps and manage campaigns
// Internet Profile Service
risk-based auth for seamless ux that's incredibly easy to deploy
// Intelligent Authentication
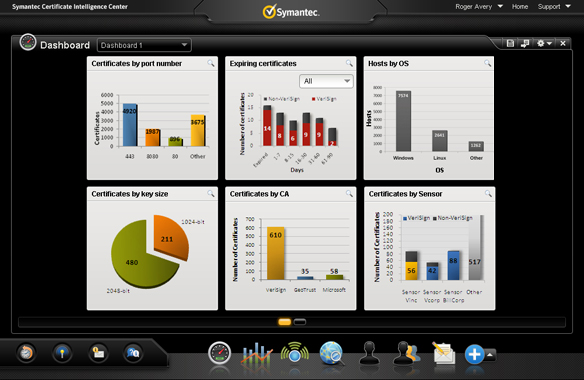
automate certificate lifecycle management for
efficiency, consistency, and accuracy
// Certificate Intelligence Center
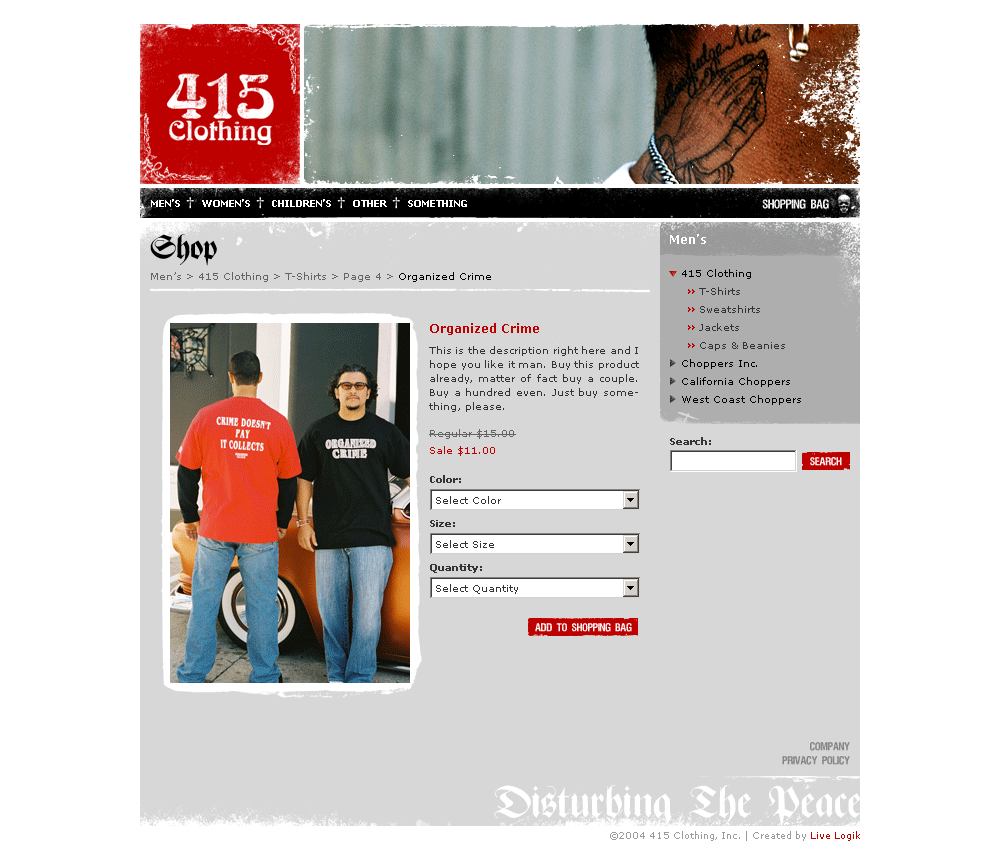
online shopping with an attitude, disturbing the peace
// 415 Clothing
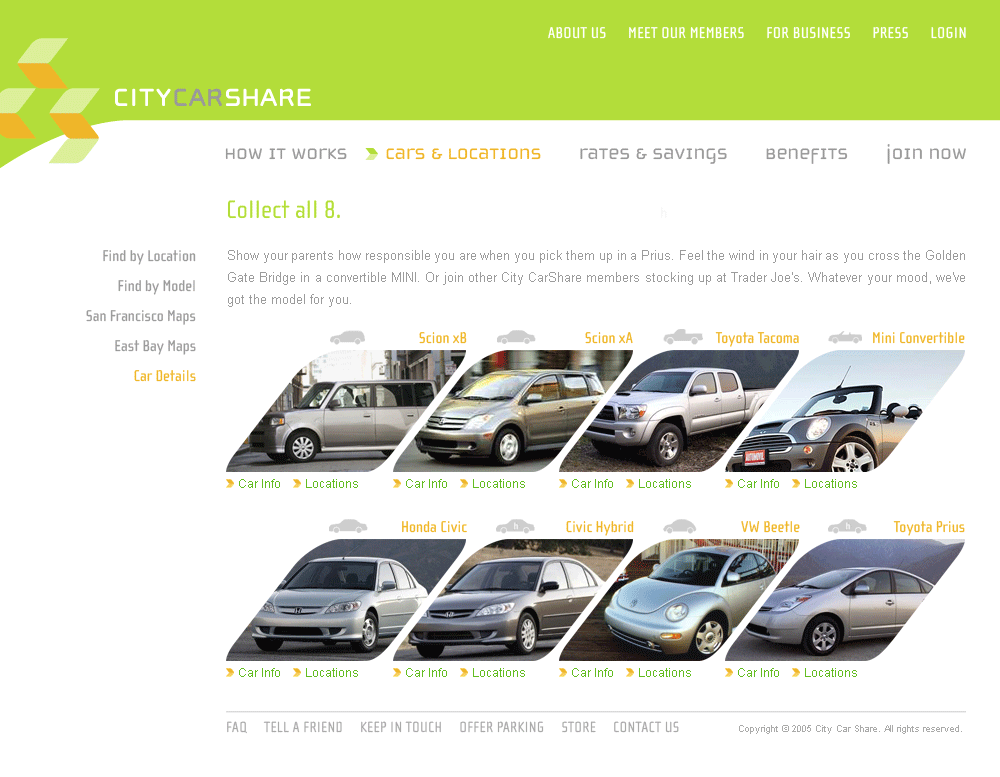
drive. return. repeat.
// City CarShare
classic
// Living Legends